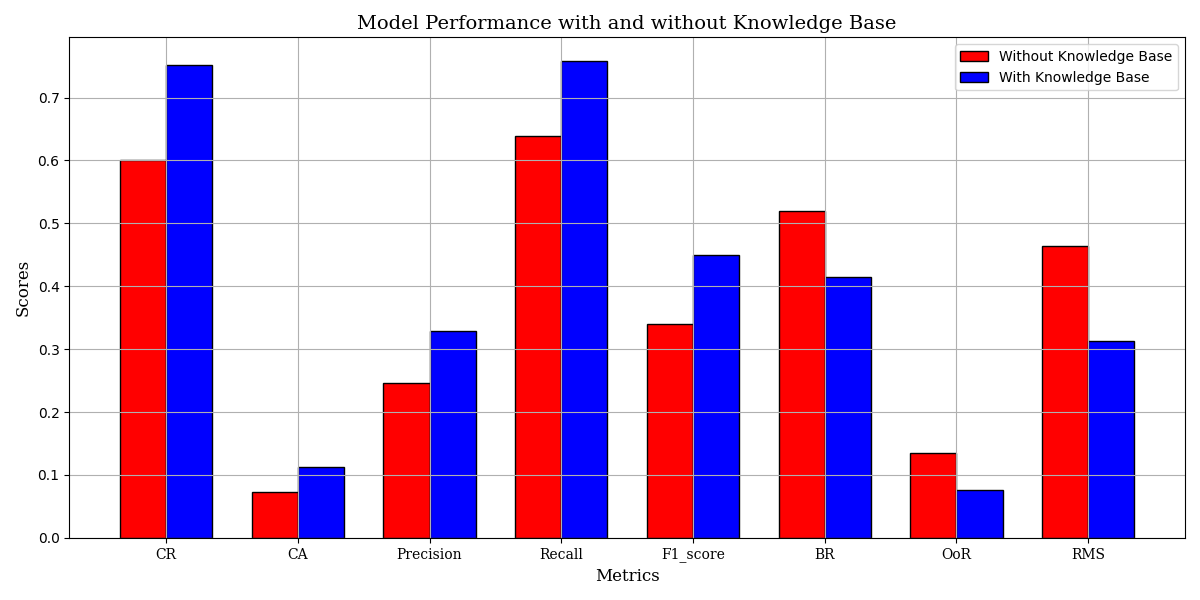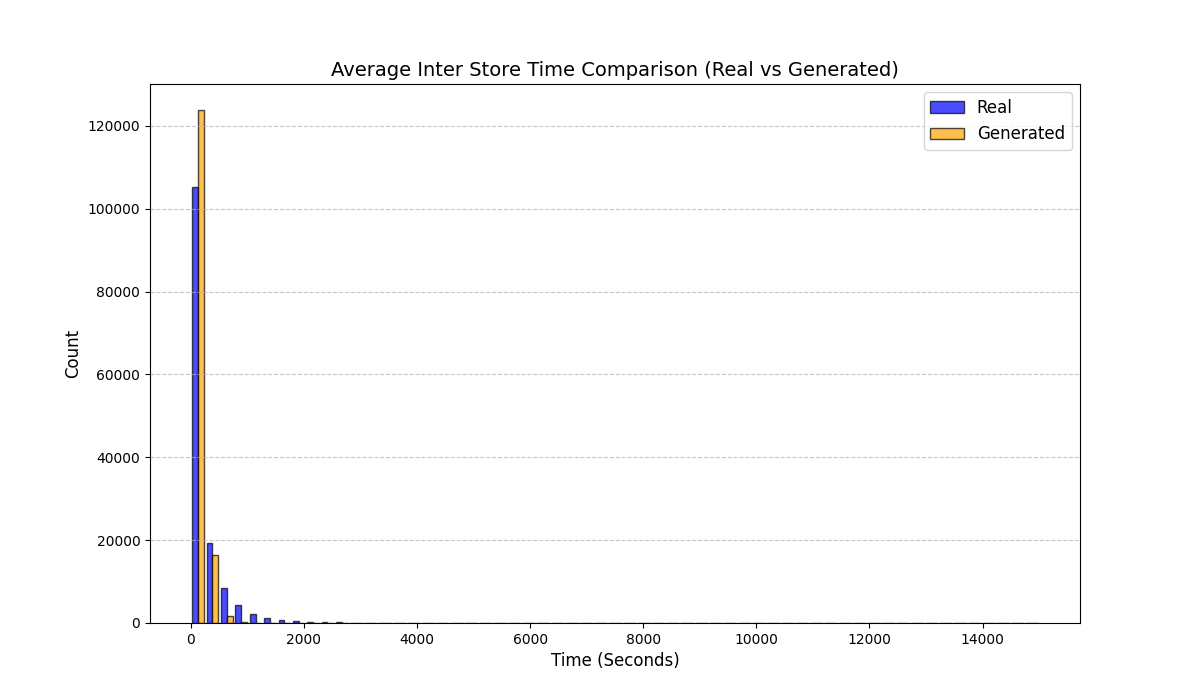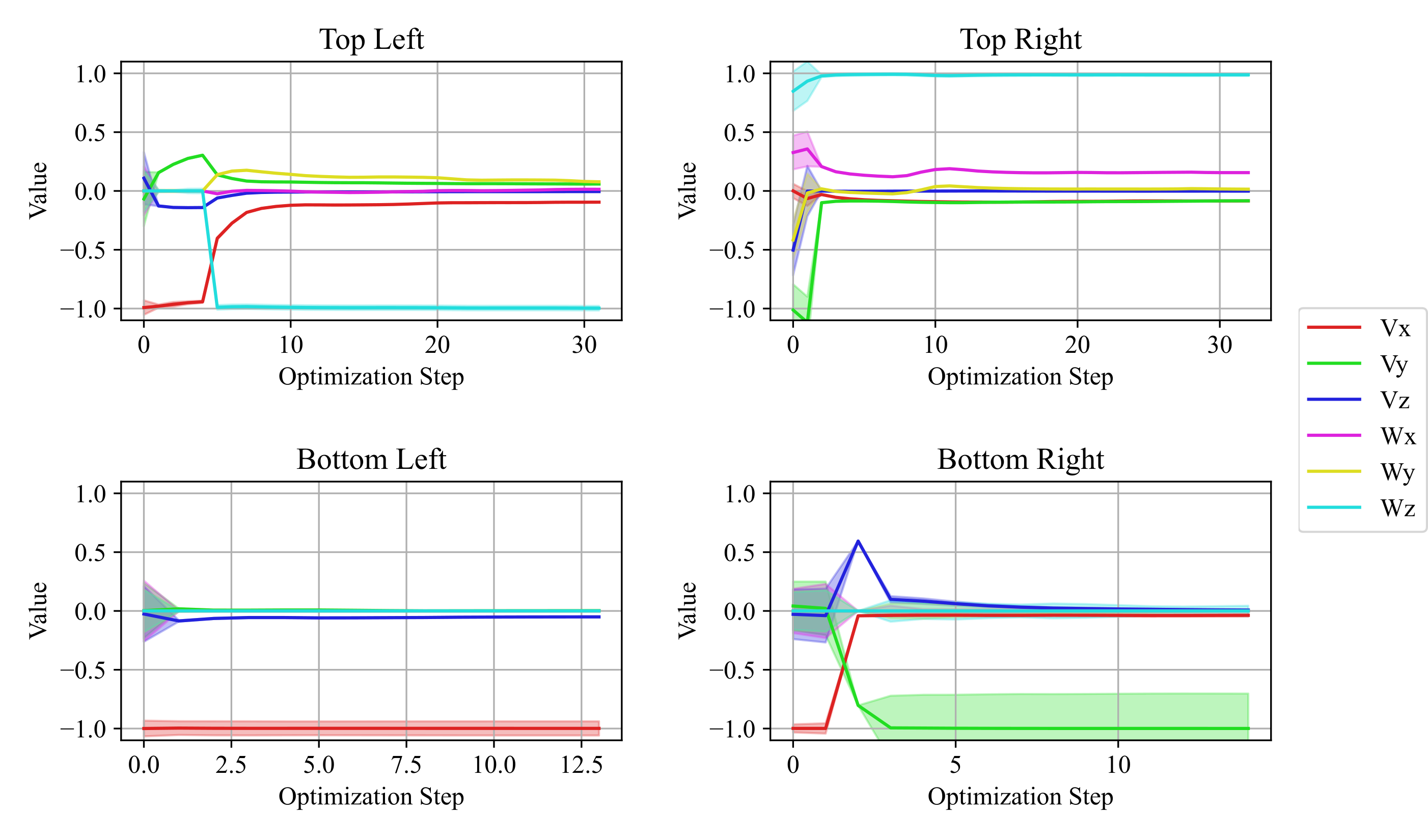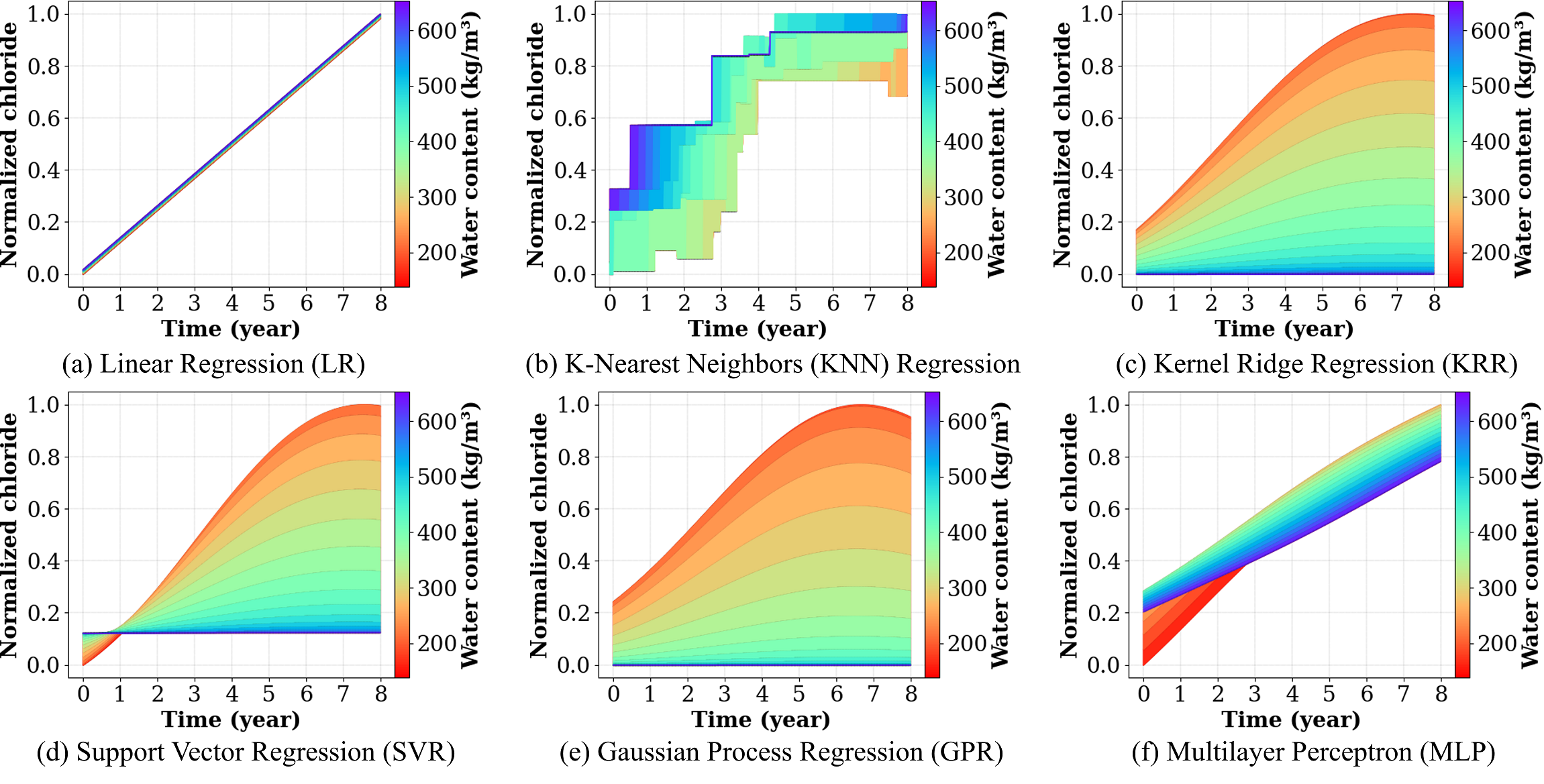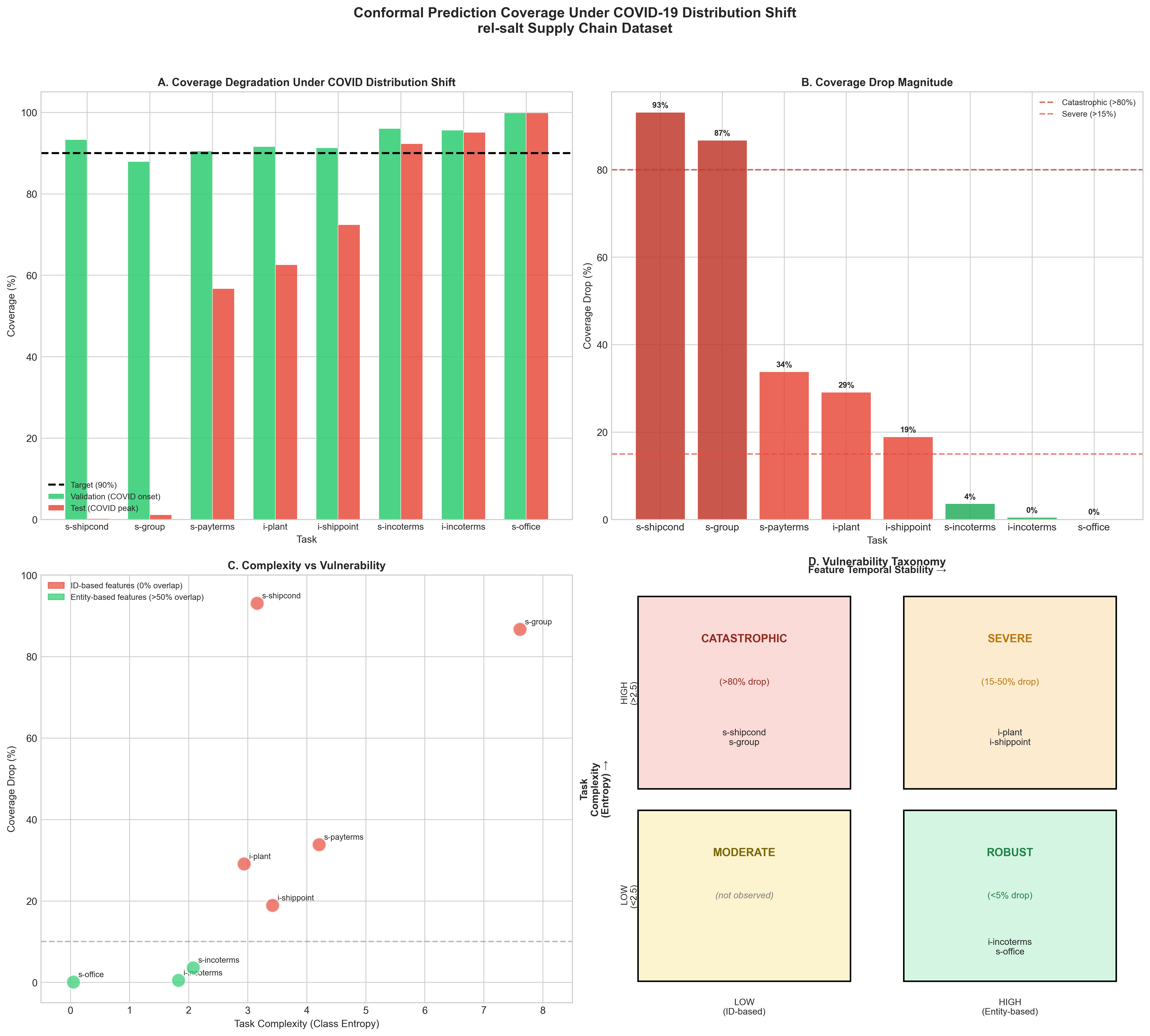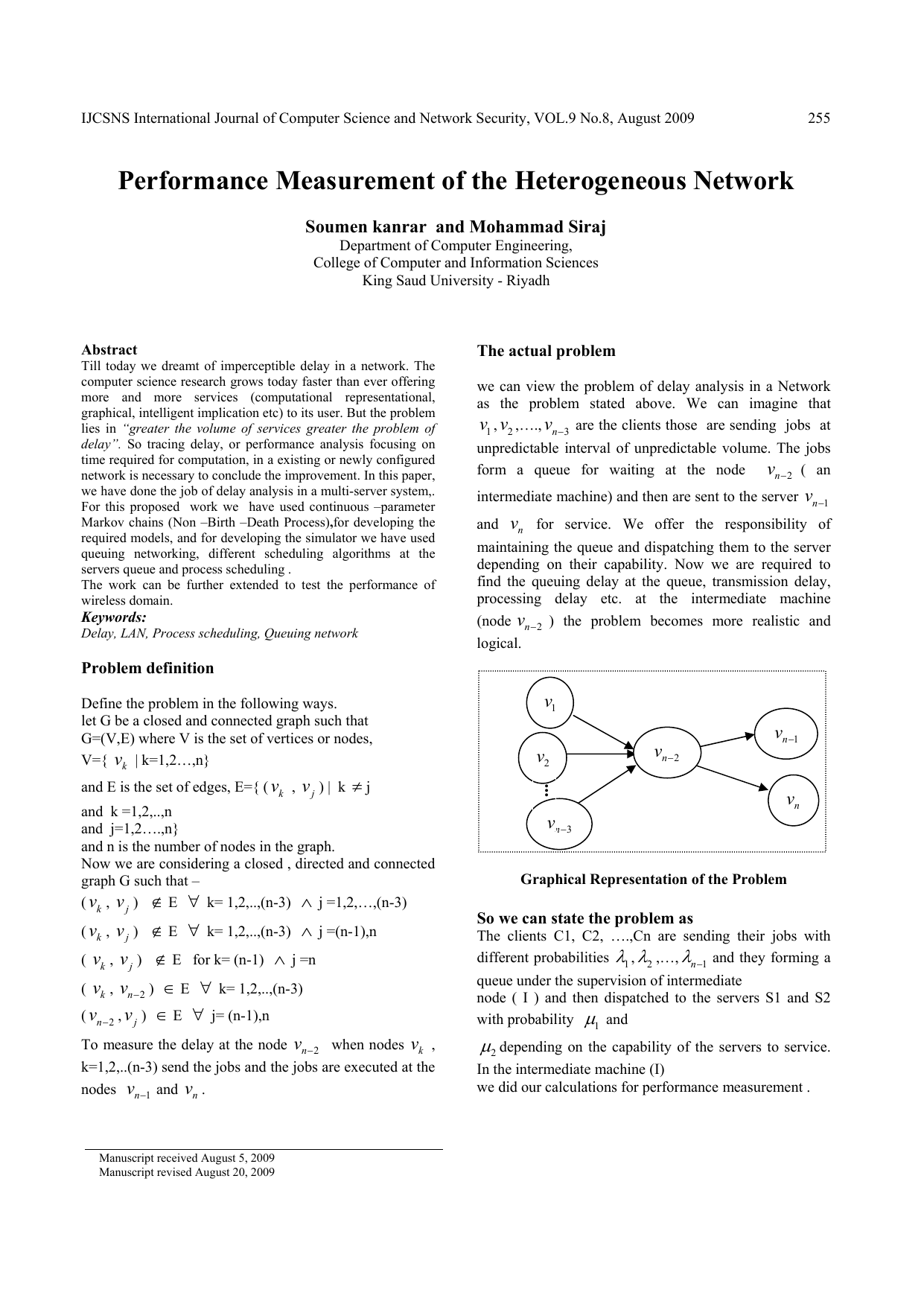
Performance Measurement of the Heterogeneous Network
이 논문은 M/M/2 큐 시스템을 활용하여 네트워크 지연 문제를 분석하고 있습니다. 이 모델은 두 개의 서버로 구성되며, 각 서버는 서로 다른 처리 능력을 가지고 있어 작업 스케줄링 방식은 FCFS(First Come First Served)입니다. 1. M/M/2 큐 시스템 M/M/2 큐 시스템은 네트워크 지연 문제를 효과적으로 모델링하기 위한 도구로, 이 시스템의 주요 특징 중 하나는 두 개의 서버가 서로 다른 처리 능력을 가지고 있다는 점입니다. 작업 스케줄링 방식은 FCFS로, 작업이 도착한 순서대로 처리됩니다. 2. 상태