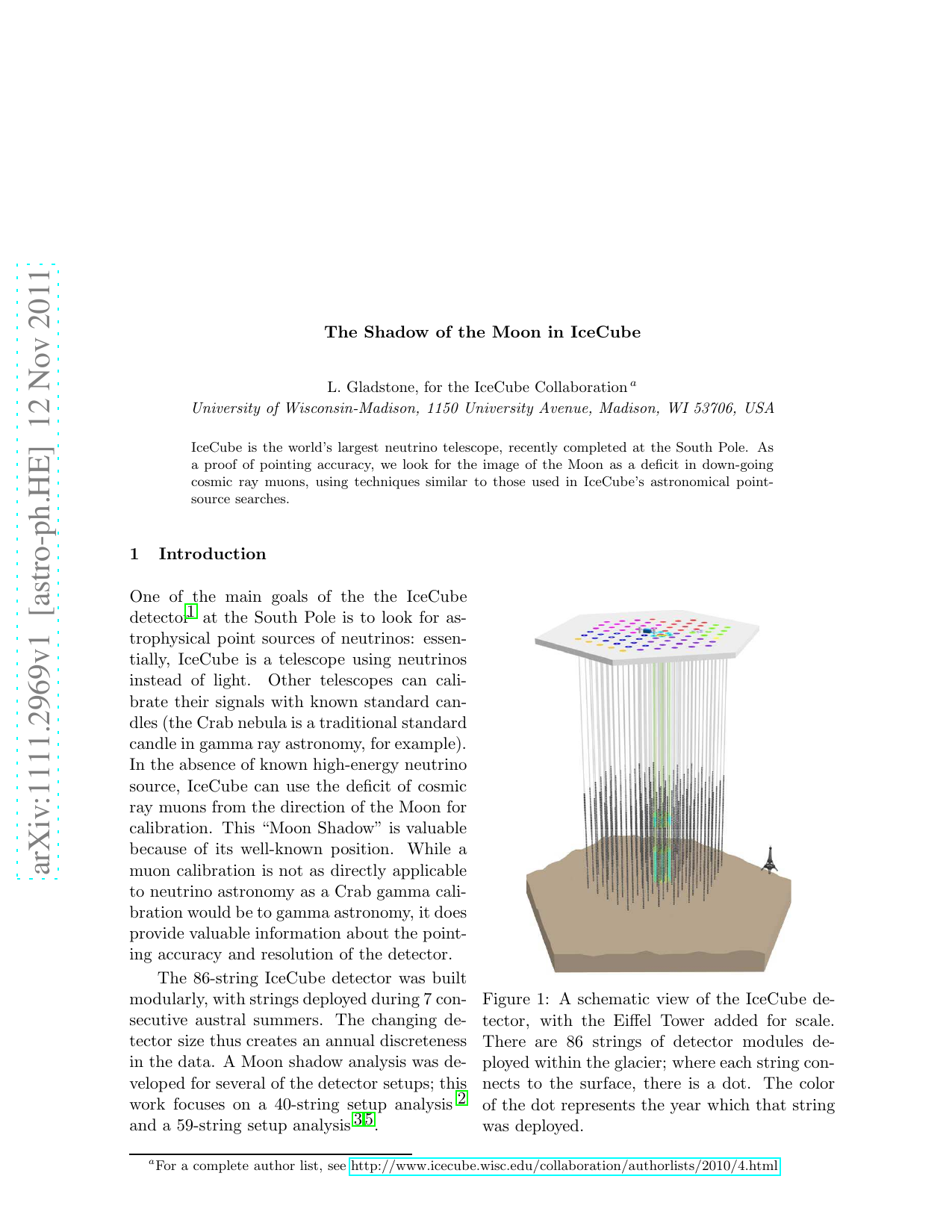
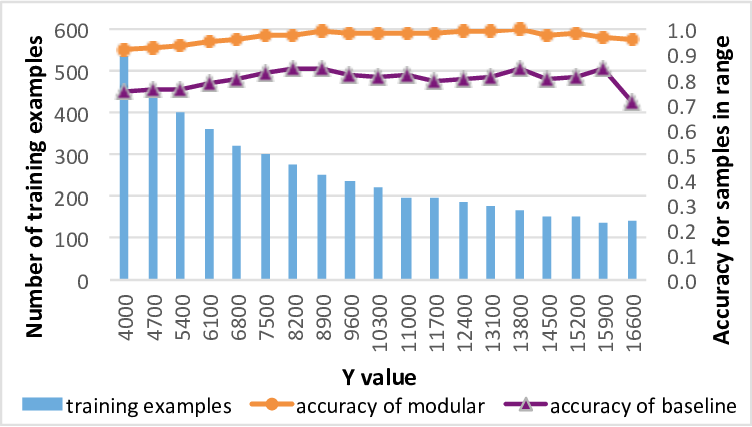
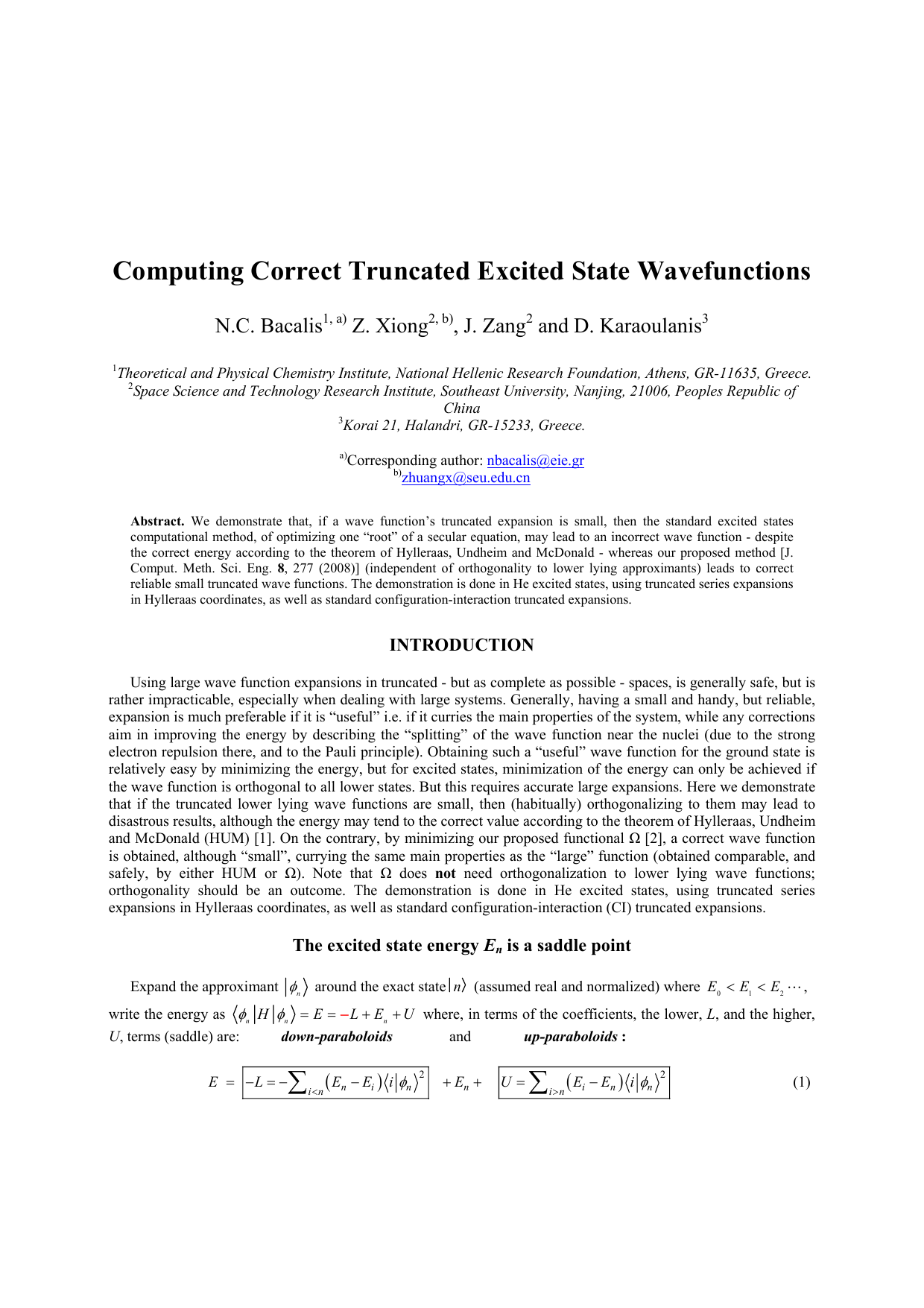
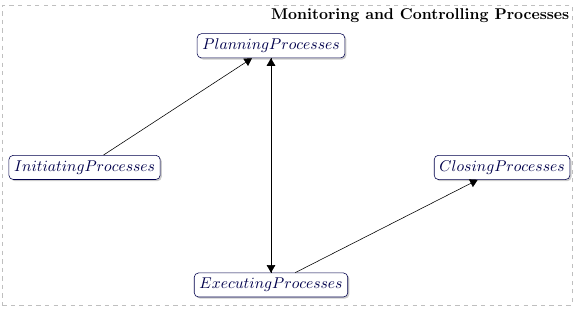
The Disp Method for Analysing Large Zenith Angle Gamma-Ray Data
1. 동기와 배경 Disp 방법은 단일 망원경 관측에서 주 감마선 방향 재구성의 기본 알고리즘으로 널리 사용되어 왔습니다(예: Lessard et al., 2001; Kranich & Stark, 2003; Domingo Santamaría et al., 2005). 그러나 새로운 세대의 지표 기반 감마선 망원경은 배열 모드로 여러 개의 망원경을 사용하여 동시 관측이 가능하게 되면서 보다 정교한 방향 재구성 기법이 필요해졌습니다. 특히, 큰 각도(LZA)에서 이러한 기법들은 성능 저하를 겪게 됩니다. 이는 공기 샤워가 IACT 배열