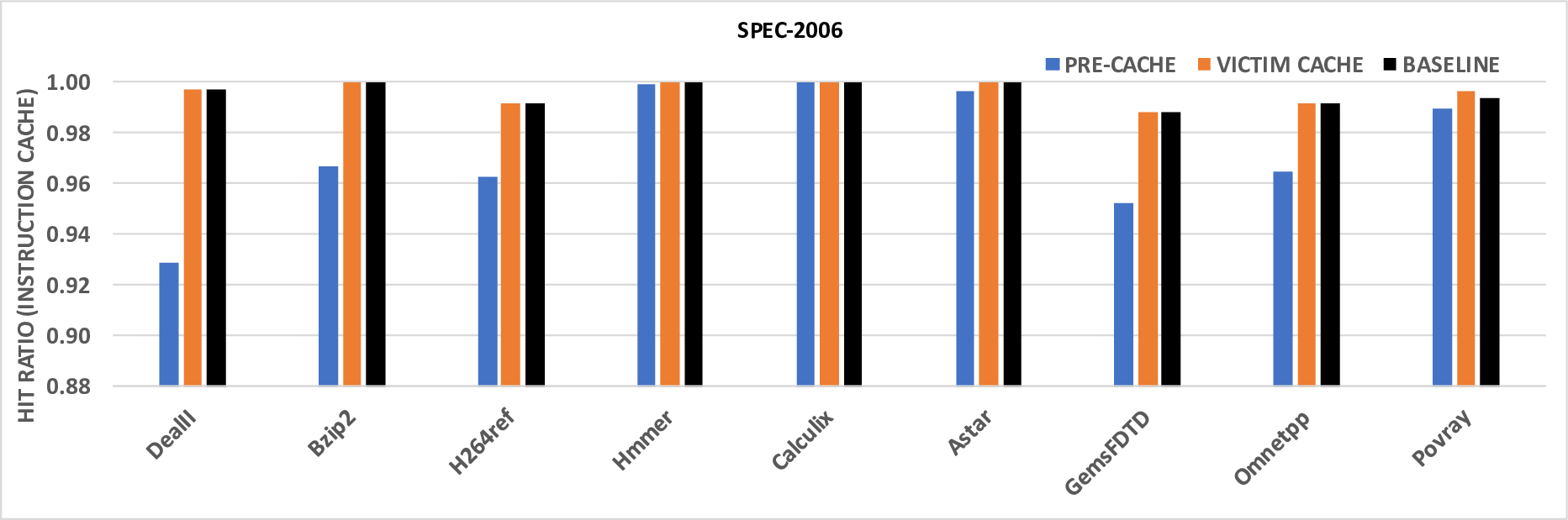
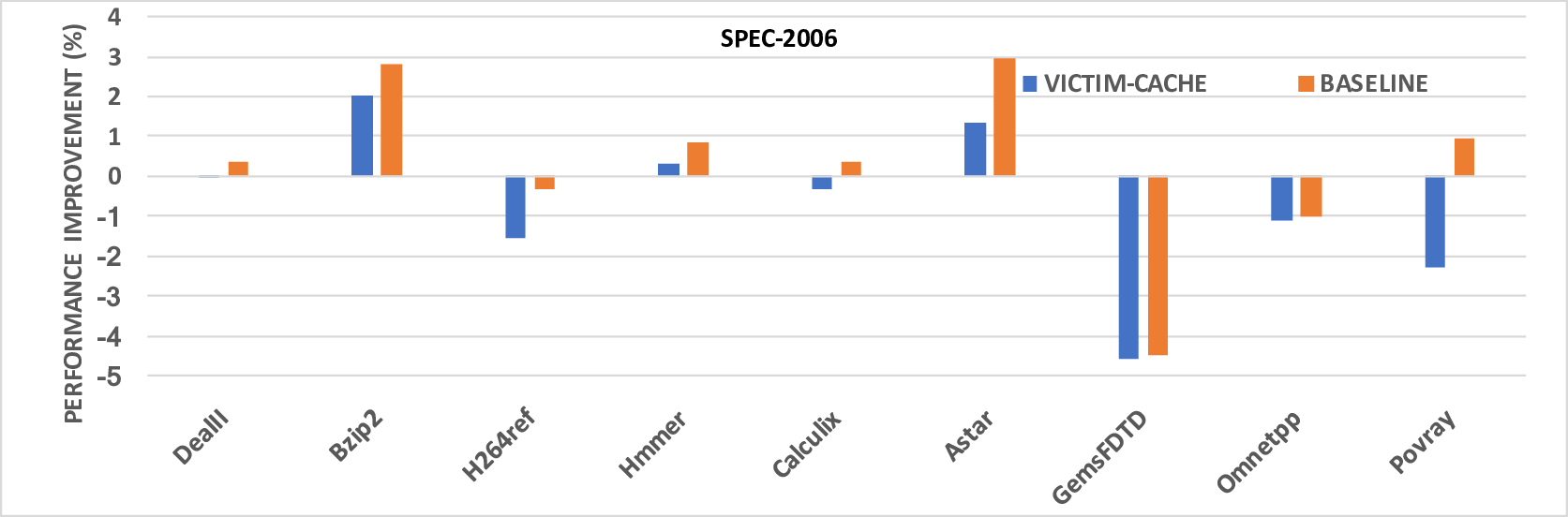
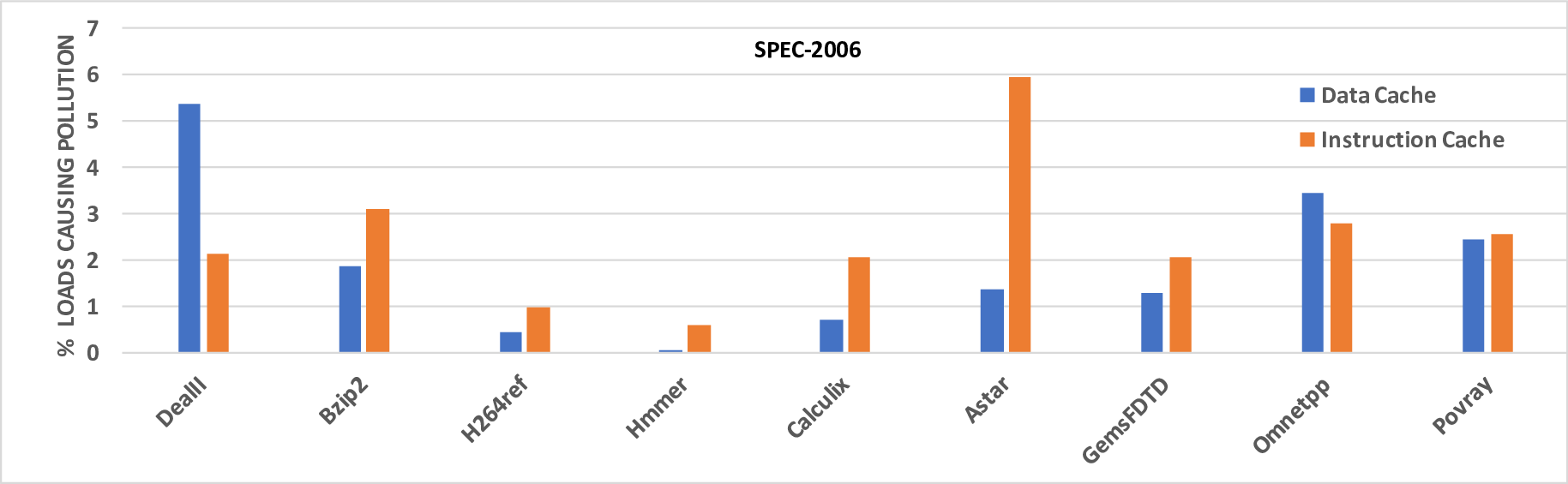
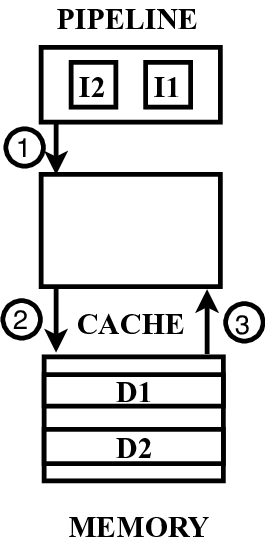
Recent work has shown that out-of-order and speculative execution mechanisms used to increase performance in the majority of processors expose the processors to critical attacks. These attacks, called Meltdown and Spectre, exploit the side effects of performance-enhancing features in modern microprocessors to expose secret data through side channels in the microarchitecture. The well known implementations of these attacks exploit cache-based side channels since they are the least noisy channels to exfiltrate data. While some software patches attempted to mitigate these attacks, they are ad-hoc and only try to fix the side effects of the vulnerabilites. They may also impose a performance overhead of up to 30%. In this paper, we present a microarchitecture-based solution for Meltdown and Spectre that addresses the vulnerabilities exploited by the attacks. Our solution prevents flushed instructions from exposing data to the cache. Our approach can also be extended to other memory structures in the microarchitecture thereby preventing variants of the attacks which exploit these memory structures. We further identify two new variant attacks based on exploiting the side effects of speculative and out-of-order execution and show how our solution can be used to prevent these attacks. Evaluation results show that our microarchitectural solution not only restores secure out-of-order and speculative execution, but also has relatively low overhead and does not significantly impact performance for most applications.
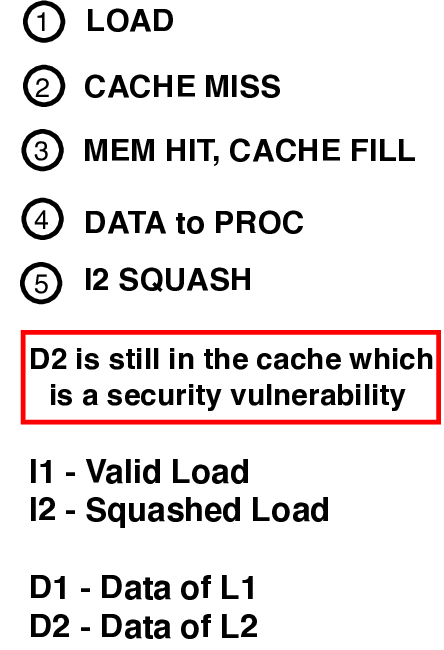
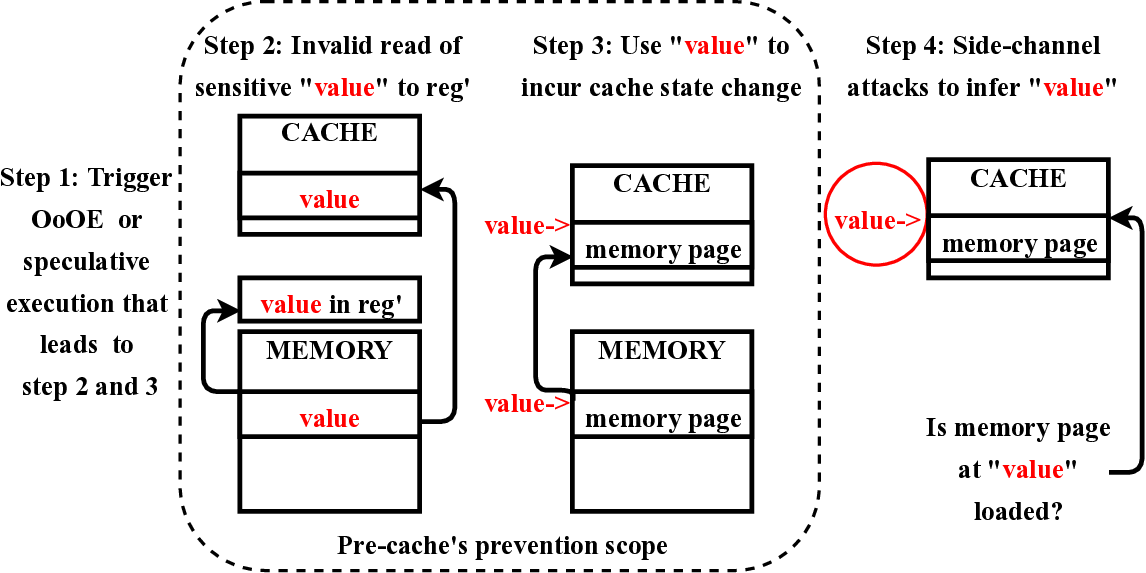
R ECENTLY, two critical security attacks have been re- ported that affect a large fraction of microprocessors used today [1], [2]. These attacks, Meltdown and Spectre, exploit fundamental vulnerabilities caused by performanceenhancing mechanisms employed in modern processors. Meltdown exploits delayed privilege checking in processors that use out-of-order execution (OoOE), while Spectre exploits branch prediction and branch target prediction mechanisms. Both mechanisms allow speculatively-executed instructions to illegally access data from unauthorized memory locations. In Meltdown [1], an instruction that is executed outof-order accesses data from the kernel memory space before being invalidated. The attack then induces state changes (i.e., side effects) in cache based on the value of the illegally-read data. While this instruction and subsequent instructions are eventually squashed, the side effects remain in the cache, which can be exploited to infer the illegally-read data using cache-based timing attacks such as Flush+Reload [3]. In Spectre [2], an instruction that is speculatively-executed based on a branch prediction and/or a branch target prediction reads data from unauthorized memory locations before being squashed. Again, the attack induces side effects in cache based on illegally-read data. Even though the instruction is not allowed to commit, the side effects remain even after the instruction is squashed, and thus can be accessed by a timing-based attack on the cache. While Meltdown reads secret data in the kernel space, Spectre can read sensitive data in the address space of another process. In addition to Meltdown and Spectre, researchers have proposed several variant attacks (Section 2.3).
Both Meltdown and Spectre are practical and critical.
They can efficiently leak secrets stored in the memory of kernel space or other running programs, such as passwords, personal photos, emails, instant messages, and businesscritical documents. Researchers have shown how to dump memory, spy passwords, and reconstruct images [1]. Meltdown and Spectre impact a variety of computing devices, including personal computers, mobile devices, and cloud computing nodes. Depending on the cloud provider’s infrastructure, it may even be possible to steal data from other customers. Security researchers consider these vulnerabilities catastrophic because they are fundamental and widespread. These vulnerabilities exist in fundamental mechanisms employed in most processors manufactured in the last 20 years [4]. As such, they pose critical security threats to most computer devices, and fixing these vulnerabilities is urgent. While reverting back to in-order execution is an intuitive and effective solution, it would lead to serious performance degradation [5]. Similarly, disabling speculative execution forfeits its significant performance benefits and is thus unacceptable [5]. Rather, an effective solution is one that allows out-of-order and speculative execution yet resolves the underlying security problems introduced by these mechanisms. While the vulnerabilities exploited by the attacks are in hardware, the attacks themselves are implemented in software. Therefore, solutions can be based on software and/or hardware. Since the threats were made public, most processor manufacturers and major system software vendors have proposed solutions to stop these attacks (see Section 2). In general, software-based solutions address symptoms (e.g., the way in which existing attacks exploit the hardware vulnerabilities) and thus are ad hoc. For example, KAISER [6] isolates the kernel page table from user space, which stops Meltdown from accessing kernel addresses directly from user space. This fixes Meltdown but not Spectre or other variant attacks [7]. Moreover, it imposes 5% performance overhead for most workloads and 30% or more performance overhead in some cases [8].
Although hardware-based fixes have the potential to eliminate the vulnerabilities exploited by these attacks, existing solutions fix only particular variants. For example, hard-split bit (preventing access to kernel addresses from user space) suggested by the original Meltdown paper [1], stops only Meltdown. Similarly, Intel recently developed a hardware solution -introducing new CPU instructions that eliminate branch speculation -to prevent the Spectre variant (Spectre V2) that targets branch target injection. Such a solution still leaves the processor vulnerable to the Spectre variant that targets bounds check bypass (Spectre V1). We conclude that to prevent Meltdown, Spectre, and their current and future variants, we need to address the vulnerabilities in hardware; we require an efficient and general hardware-based solution that eliminates the vulnerabilities exploited by the attacks.
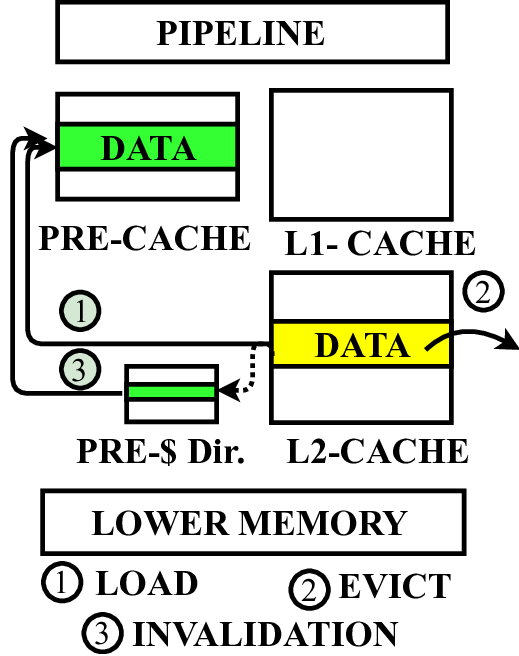
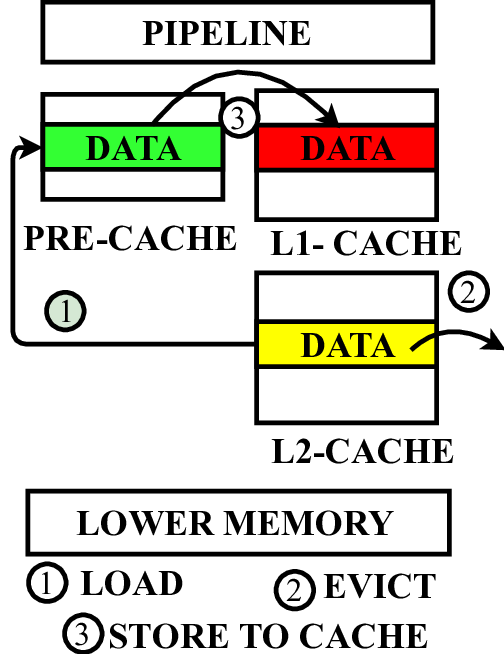
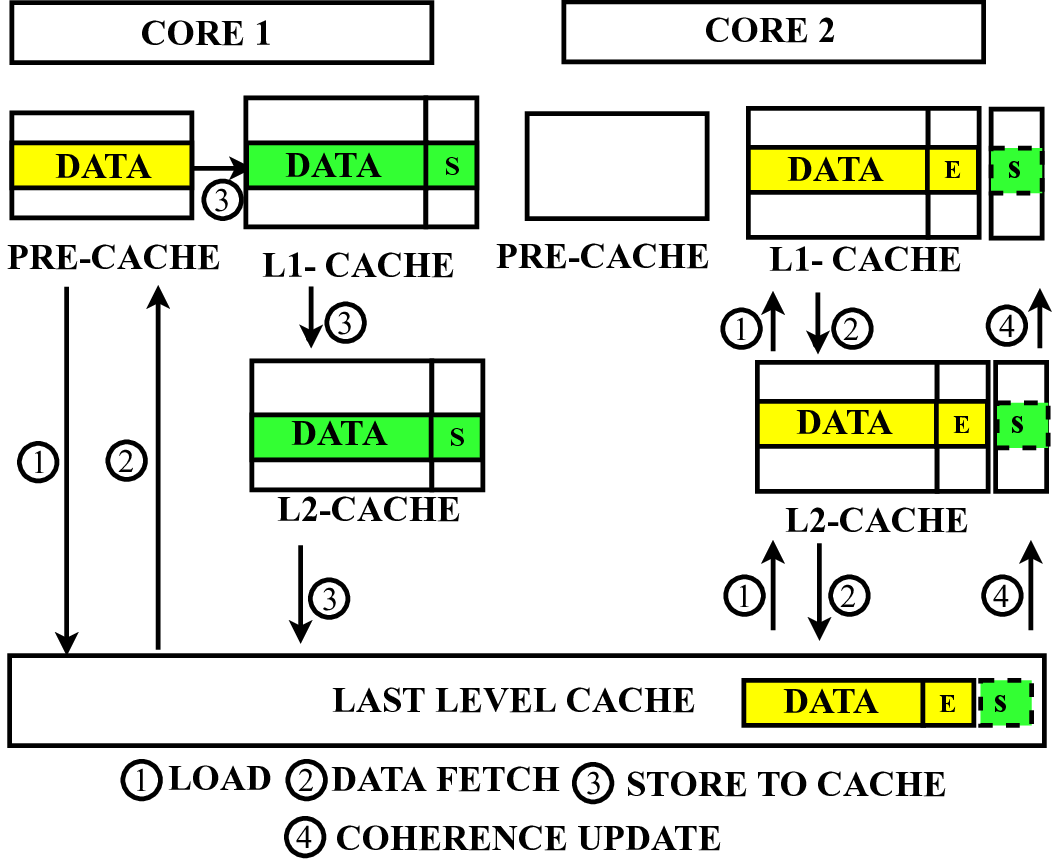
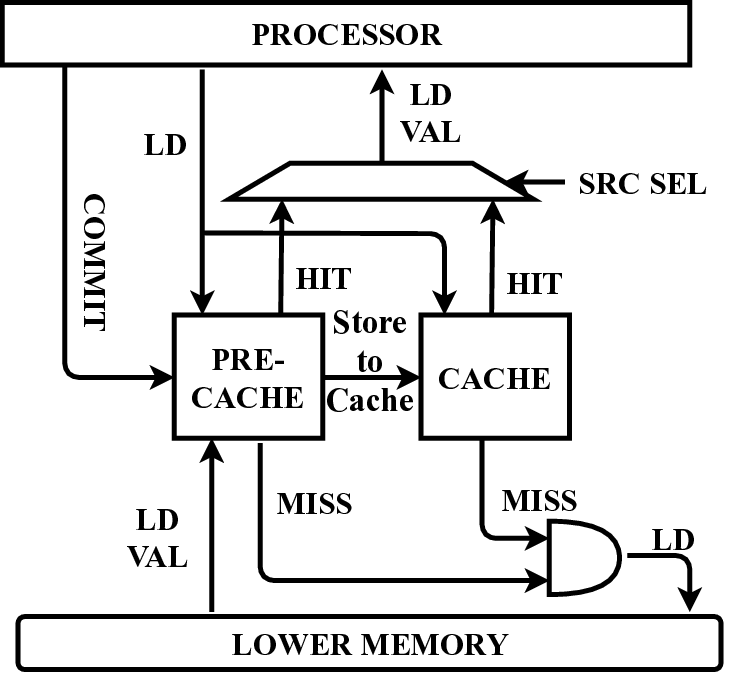
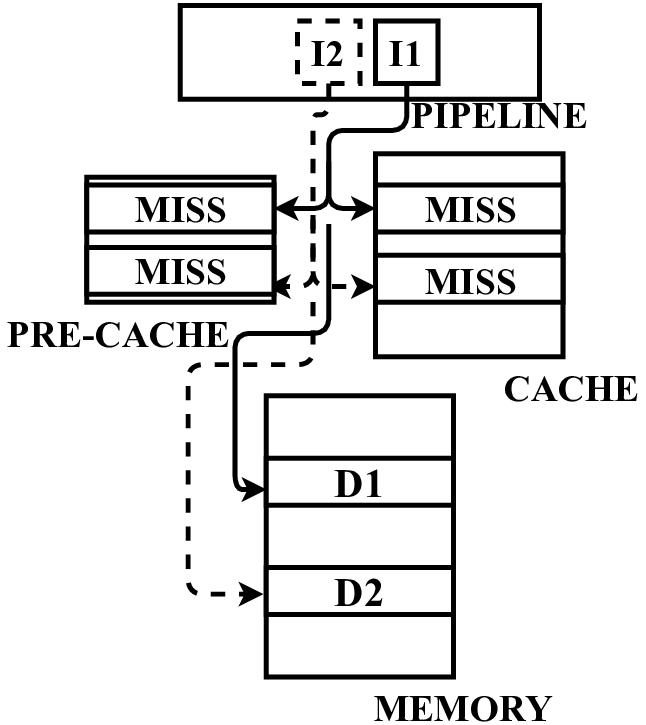
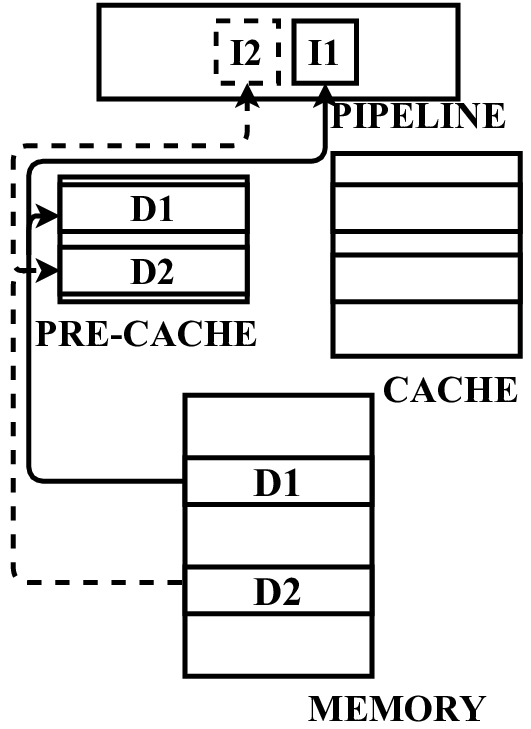
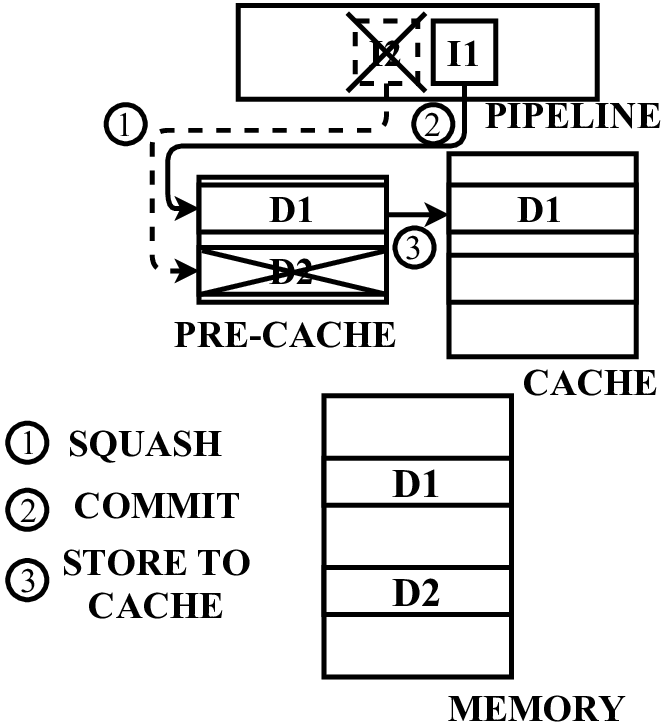
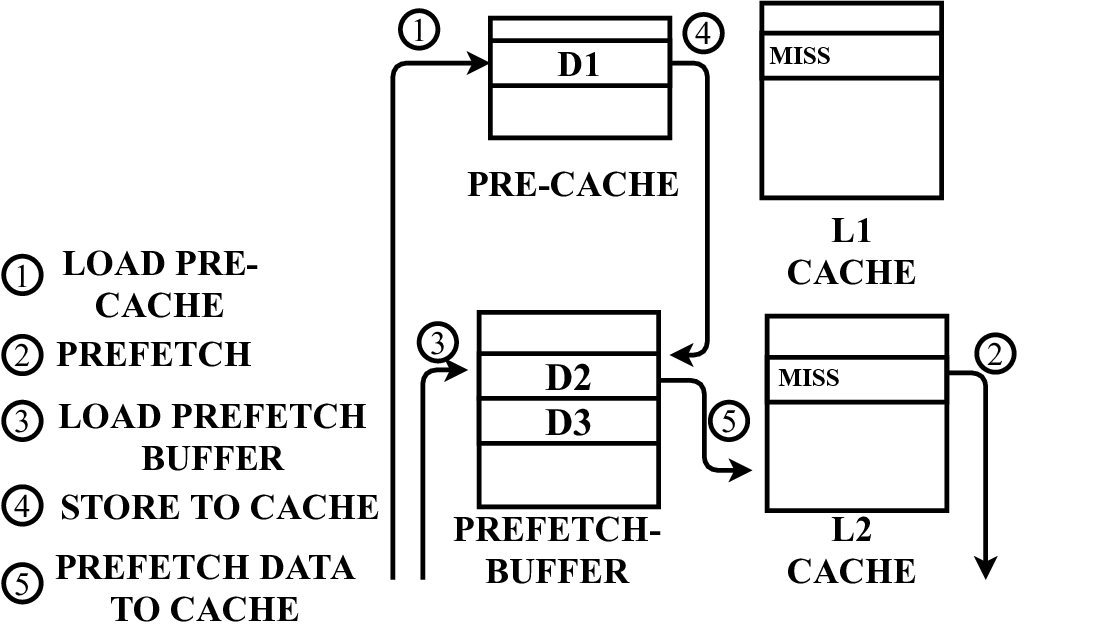
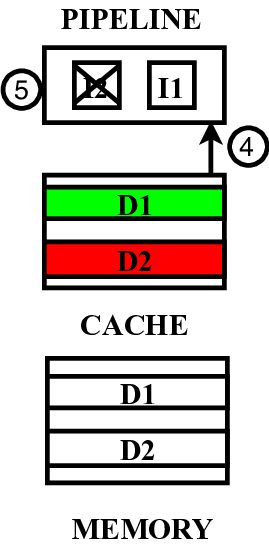
In this paper, we propose a microarchitecture-based solution -Pre-cache-to comprehensively prevent Meltdown, Spectre, and their variants that exploit the memory structures in the pro
This content is AI-processed based on open access ArXiv data.